The Problem
I have an older, out-of-warranty MacMini whose WiFi is acting flaky after the recent upgrade to OS X Lion. This wouldn’t be a problem in most places in the house since we’ve got wired gigabit connections in most rooms, but this Mac sits on my youngest child’s desk and, after a recent rearrangement of the kid’s office, this desk happens to be on the opposite side of the room from the wired Ethernet jack. After rearranging the room, but prior to the Lion upgrade, the WiFi was working just fine for getting that particular Mac connected to the Internet.
The immediate fix was to run a fifty foot patch cable from the Ethernet jack over the door, around the windows, and along the baseboard to the desk. Expedient, but not very decorative. I knew this had to be temporary and that’s what I told the darling wife. At the time I said it, I hadn’t formulated the eventual solution, but I did have vague recollections of reading about the various modes available with the Apple AirPort Express Base Station (AEBS).
As it turns out, the ProxySTA mode is exactly what I needed to solve this problem, the most succinct explanation of which I found in a TiredDonkey blog post.
Some Background
My WiFi setup consists of a Time Capsule (TC), an Airport Extreme in the north end of the house, and another in the south end. All three of these devices are configured to “Create a wireless network” with the same network name, enabling roaming on a single network throughout the house.
The TC is located in the basement next to the cable modem and is configured as the DHCP server for the house. The TC also serves up the guest network. The Extremes are both configured in bridge mode to pass all DHCP-related traffic to the TC. They are all connected via gigabit. One of the great features of the newer Time Capsules and Extreme base stations is that, when configured to serve up the same network, they also synchronize their Access Control lists–a configuration change in the access list on one device is shared with the others greatly simplifying maintenance.
A number of AEBSes scattered throughout the house complete the setup providing whole house audio via AirTunes. One of these AEBS is used to provide the bridge to the MacMini.
Back to the Problem
As I was following the instructions in the blog post I was skeptical because the instructions explicitly state turn off access control–I am security conscious and not only do I have WPA2 password protection on my networks, I also use access control to deny access to unknown WiFi devices.
As I expected, this solution, as written, did not work for me. Due to my security precautions the AEBS was not connecting to the WiFi network.
As it turns out it wasn’t just the access control, but my larger WiFi infrastructure (beyond the single Express, single Extreme setup in the blog referenced above) that caused the failure.
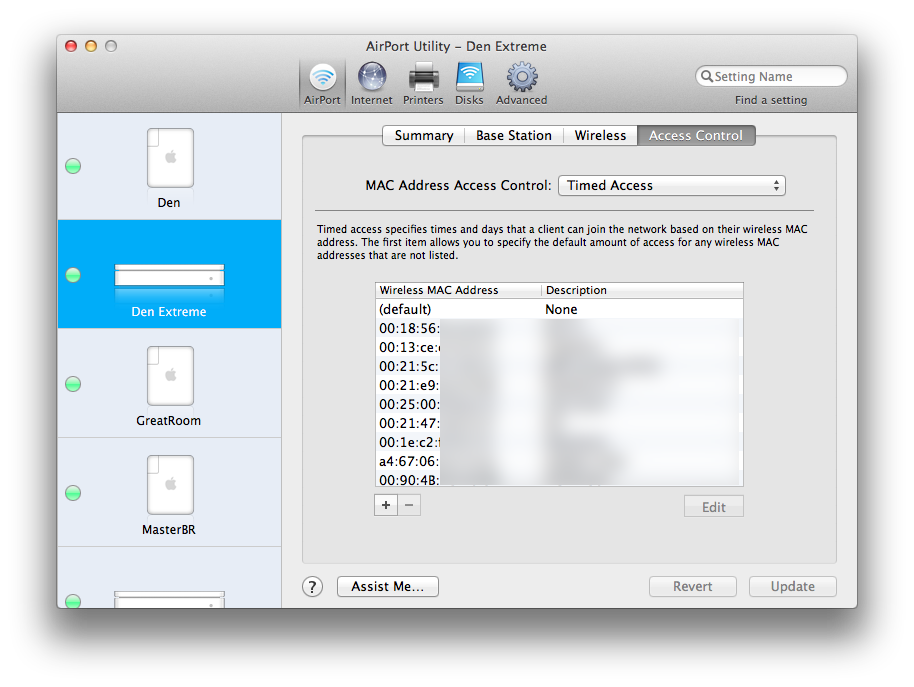
The first difference between my solution and the blog post referenced above is the setting of Mac Address Access Control to Timed Access:
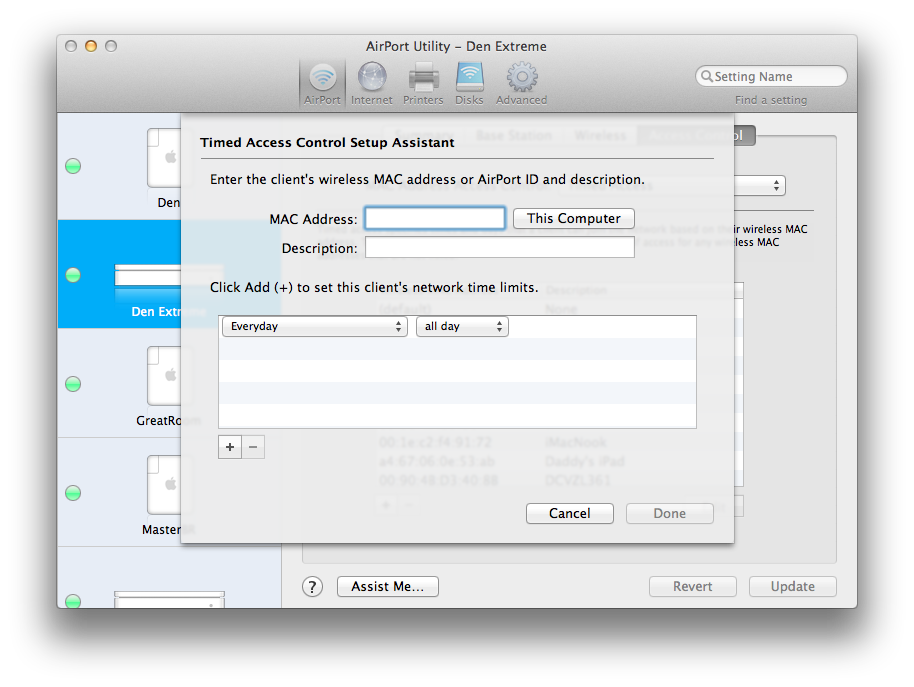
Adding the Airport ID of the AEBS to the access control list (ACL) to allow 24×7 access (add Airport ID in MAC Address field below) was necessary:
It was also necessary to add the MAC address of the Ethernet port of the device being connected to the AEBS to the access control list. This would allow the access point to reply to the DHCP requests from the device connected to the AEBS via Cat-5. If you have assigned a static IP to this device, then adding this MAC to the ACL is not necessary.
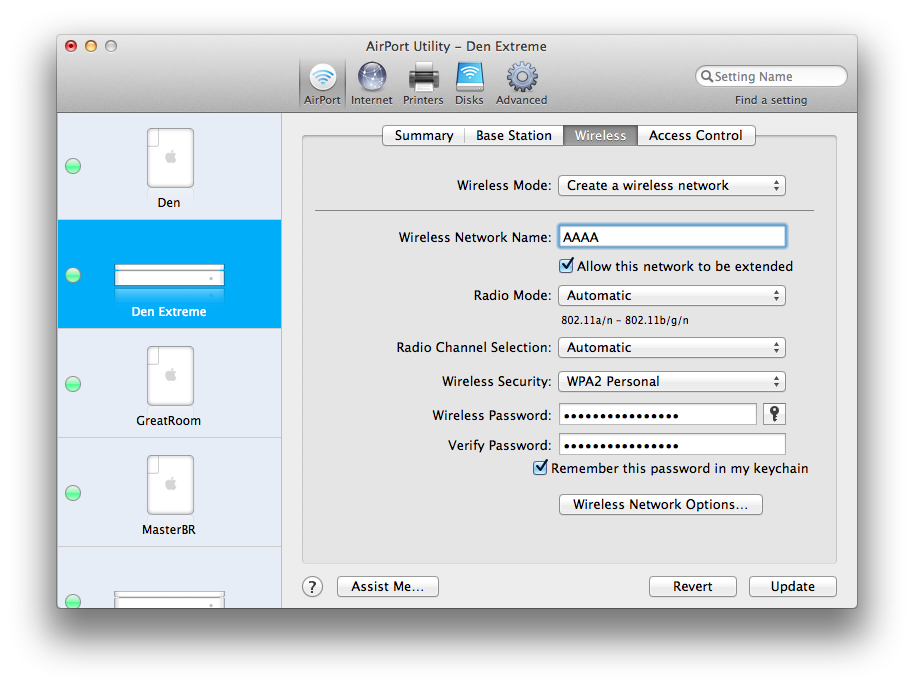
I added the access control entries to the Den Extreme base station which I knew would be closet to the AEBS, I also ensured the Allow this network to be extended box was checked for the same Extreme on the Wireless tab:
I thought that this would be it and I would have my connection. As it turns out I was wrong.
Almost There
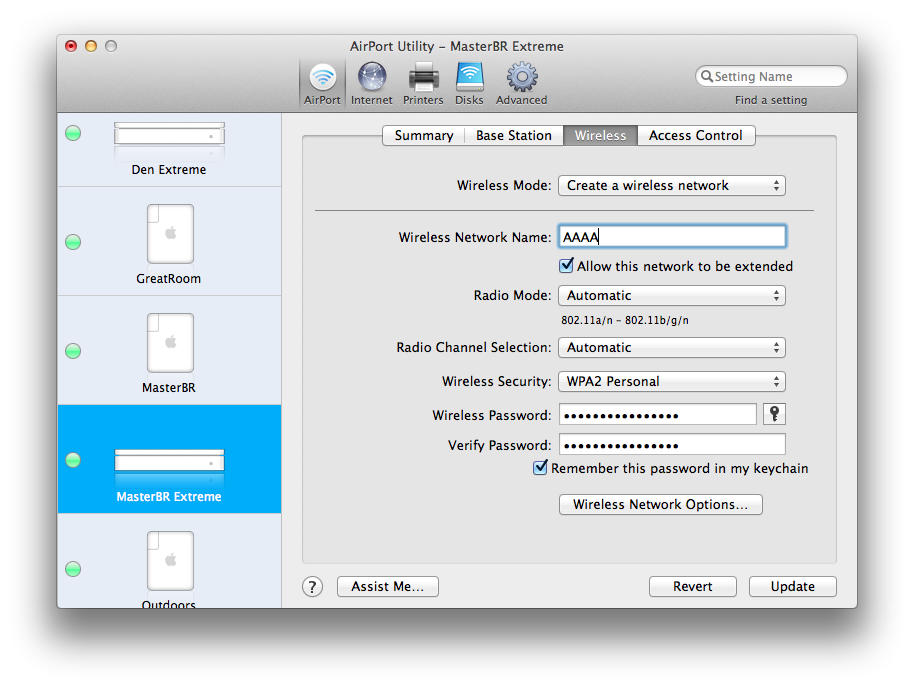
I checked the AEBS to make sure that it was in fact a client of the Den Extreme base station, and it was. I then rechecked the access control list in the Den Extreme and it still contained the AEBS AirPort ID–that configuration was saved properly. It then occurred to me that I should check the access control lists on the TC and the other Extreme base station. As expected, they both had inherited the changes to the access control list allowing the AEBS access. What was different is that the Allow this network to be extended box was not checked on these other devices. So I checked the box on the second Extreme base station:
and on the Time Capsule:
After saving these configurations and allowing all the base stations to restart I finally had my solution.
In Short
The solution consists of:
- Starting with the blog post as referenced above
- Adding the AEBS AirPort ID to the Access Control List (ACL) for the wireless network, as well as the MAC address of the connected device (if not assigned a static IP)
- Ensuring Allow this network to be extended is checked on all wireless base stations serving the wireless network